Manage your testing
in one place
Our easy-to-use platform lets you track progress, review vulnerabilities, and action fixes.
Easy reporting
Access detailed findings, risks, and remediation steps directly through the Atlas hub.
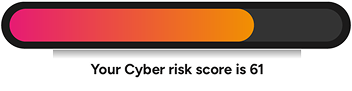
Simplified dashboard
Effortlessly track your testing progress to allocate resources efficiently.
Compare results
Review past tests to spot recurring vulnerabilities and track improvements with a full audit trail.

Web application scanning
Stay proactive by continuously monitoring to find new threats to your applications.


What you can test
Our penetration testing services let you test anything that connects to the internet. These tests uncover vulnerabilities and allow us to deliver tailored recommendations that safeguard sensitive data and the systems supporting it.
Network Infrastructure
Identify risks with expert-led simulated attacks to protect your data and systems.
Wi-Fi Network
Stay protected between pen tests with continuous scanning and real-time breach alerts.
Mobile App and Devices
Tailored advice for compliance, ransomware plans, and board-level cyber support.
Types of Penetration Testing
Before any testing takes place, you’ll have a 1:1 scoping session with one of our ethical hackers to discover the best approach for your business
Provide us with full network and system information, giving the most thorough evaluation.
Provide us with limited network and system information to mimic an authentic insider threat attack.
Provide us with no information about your systems and networks to simulate an authentic cyber criminal attack.
Simple five step process for thorough penetration testing
- Provide us with information on all systems in scope for testing.
- Our licenced penetration testers will assess the in-scope items and identify vulnerabilities.
- Controlled attacks are performed to gain access.
- We’ll compromise as many privilege accounts and systems as possible while maintaining access.
- Following the test, you’ll receive a full report detailing the findings and a free remediation retest.
Save more with penetration testing bundles
Why not make protecting your business simpler and more affordable? Our penetration testing bundles make that happen.
These packages are a flexible, budget-friendly way to strengthen your security as part of your managed service. You can split your days across testing solutions at a discounted rate. And, the more days you include, the more you save, with up to 30% discounts.
Can you afford a security incident?
Before any testing takes place, you’ll have a 1:1 scoping session with one of our ethical hackers to discover the best approach for your business
average annual cost of cyber crime per victim
Instances of cyber crime across all UK businesses in the last 12 months
The UK is the most cyber attacked country in Europe, accounting for 43% of all cases
days on average for businesses to identify and contain security breaches
Frequently Asked Questions
Manual tests involve skilled professionals who personally explore and exploit vulnerabilities. This gives you deeper and more accurate insights into your system’s security. Automated tests use software tools to quickly scan for known vulnerabilities, which makes them faster and more affordable. But they can miss complex issues or flag false positives. Automated testing is great for a quick, broad overview of large systems, while manual testing takes more time and investment but provides a detailed, tailored evaluation and a realistic simulation of potential cyber attacks.
We make sure our assessments cause minimal disruption to your day to day operations. If you prefer, we can perform testing within UAT, staging, or development environments. Any security issues we find, we report to you in real time. This means you can take swift action before they’re found or exploited by malicious actors.
Yes, absolutely. You’ll have direct access to the penetration tester throughout the engagement. This includes initial discussions in the scoping phase, optional daily summaries during testing, and a debrief or “wash-up” call after we deliver the report to walk you through the findings and answer any questions.
We focus on delivering meaningful results, not just ticking boxes. We tailor the test to your environment and risk profile to make sure you’re only paying for what you actually need. You’ll receive clear, actionable insights – not just technical jargon – and a follow-up session to help you get the most value from what we find.
We’ll update you throughout the process. If we find any critical issues during testing, we’ll let you know immediately so you can take action. And when we complete the test, you’ll get a full report and a debrief sessions to go through the findings and recommendations in detail.
Yes, we offer a complimentary retest of all critical and high-risk vulnerabilities within 30 days of the initial test. This allows you to verify that key issues have been properly resolved – at no extra cost.

Why our customers love us
Expert protection against cyber threats











